If you know how to do some creative looking around on the Internet, it is truly shocking just how much access you can get to systems without really trying. Recently an Internet Security Expert Paul McMillan (@PaulM) build a tool to scan for machines which were exposed to the Internet and which didn’t have any security in place so that if you knew they were there would simply allow you to access them. What was found, and the screenshots which were published are a shocking display of systems security failure.
You would think that various colleges around the US would have a better idea of network security, but apparently not. Now these aren’t really all that important, and it would slightly embarrassing at worst if someone started making changes to these. However not everything that was found was so.
 A kiosk at a college |
 Something else at a college |
 Display board of a college library |
 A desktop at a college |
There’s some stuff that could have a direct impact on peoples day to day lives. Such as the controls for a grain silo, which I could be told to dump all the grain from the silo onto the ground, which would ruin the grain and cost the farmer a lot of money.
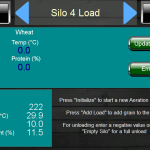
Appears to be a Grain Silo
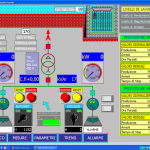
Or we could lock down the pumps at this gas station.
A large Gas Station
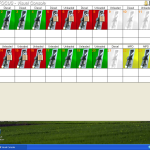
Ever wanted to control a car wash?
A Car Wash Control System
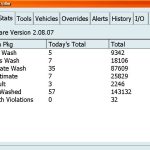
How about a movie theater?
Cinema City Movie Theater Control System
Or maybe we could screw around with the Parking ticket Kiosk for the city of Oakland, California, USA.

City of Oakland Parking Ticket Payment System
There were a large number of people’s desktop computers just sitting there available. In this one the person is writing code for an application.
Someone actively writing code
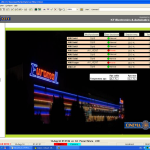
It isn’t just small companies that have their systems exposed to the Internet for no reason at all. Here’s the Double Tree hotel in Boston, MA (a member of the Hilton family of hotels). This system happens to be the display board for what’s going on in the conference rooms on the day the screenshot was taken.

The Boston Double Tree’s conference room TV
So far all of these systems have been pretty harmless. But there are some pretty big control systems online as well. Here’s the control systems for a hydro-electric plan which is producing around 480kw or power.
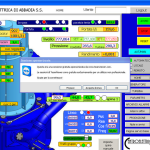
Some sort of Hydro-electric plant generating about 480kw of power
Here’s what appears to be another power plant.
My best guess is a power plant
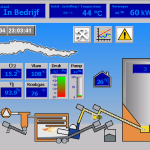
Or if coal mining is more your speed, this appears to let us control the loaders, belts, trains, etc. for an active coal mine.
Coal Mine Control System
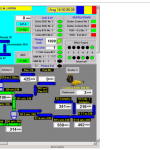
Here’s the control systems for a few more power plants, all of which are available to anyone who knows how to look for them.
 A Power Plant |
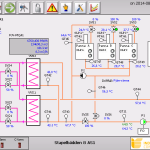 Another Power Plan |
 Yet another power plant |
I’m not really sure what this controls, but it looks pretty important.
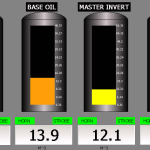
Something very industrial looking
I wonder what kind of wells these are that we can shutdown? Water, oil, could be anything.
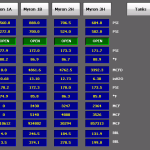
What appears to be a well monitoring system
Maybe there’s someone important hooked up to this heart monitoring system at a hospital.
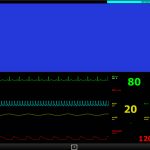
Heart Monitor for a hospital bed
Every one of these systems can be connected to, and controlled from anywhere in the world because they don’t have even the most basic network security setup on these devices. Do any of these devices need to be connected to the public Internet? No, there’s no valid reason for a single one of these to be on the Internet, but they are.
Companies who run these systems need to take better care of their networks, because eventually someone who is looking to do some actual damage is going to stumble across the tools and techniques which are used to find and access these systems. And once that happens it’s to late. Thankfully Paul McMillan was just doing research, imagine if his plan was to do actually do damage. I’ve shown you just some of the power plants, hospital equipment, and food storage locations which he found. It would have been a simple task to just shutdown all those systems one by one as he found them and no one would have had any idea that it was him, or even what happened. According to all the logs at the power plants someone would have issued the shutdown command from which ever control system that Paul was connected to.
Someone needs to get the message out to these companies, utilities, etc. that they need to fix these problems BEFORE it’s to late, not after.
Denny
Special Thanks to Paul McMillan for doing the hard work of scanning all these systems, and to Information Security Expert Dan Tentler (@Viss) for sifting through and finding some of the interesting ones and sharing them with me for this post.http://basicsofdigitalprivacy.com
Like this:
Like Loading...
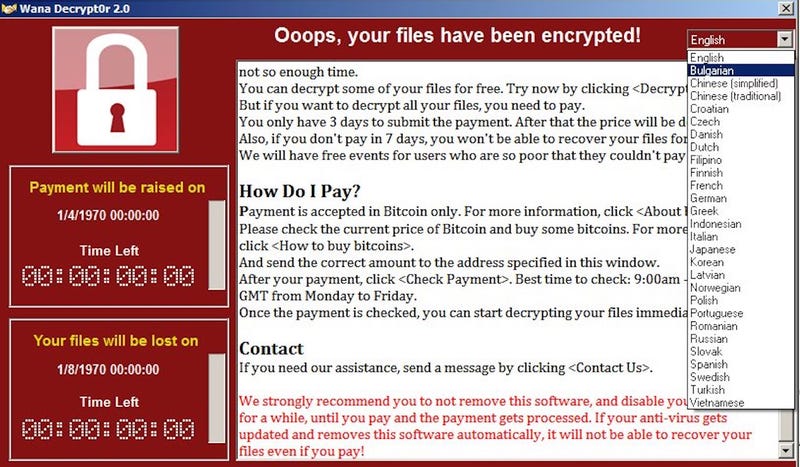 Screenshot: MalwareHunterTeam (via Gawker)
Screenshot: MalwareHunterTeam (via Gawker)